Setting up the Google Cloud App
Create a google project: https://console.cloud.google.com/projectcreateEnabling the People API
Enable the Google People API here: https://console.cloud.google.com/apis/library/people.googleapis.com Be sure to have the right project selected.Setting up the OAuth Consent Screen
Go to APIs & Services on the left hand tab (see image below). Then select OAuth Consent screen page. Under OAuth Consent screen select either Internal or External
Under OAuth Consent screen select either Internal or External
- Companies with a Google Workspace should choose
Internal - Otherwise choose
External
- Provide an app name (can go with
RECAP) - Provide any email you own (or meet@RECAP.work if you want us to handle questions from your RECAP users)
- Upload the RECAP logo (or leave blank)
- The Developer contact information can be any email you own (or again, meet@RECAP.work)
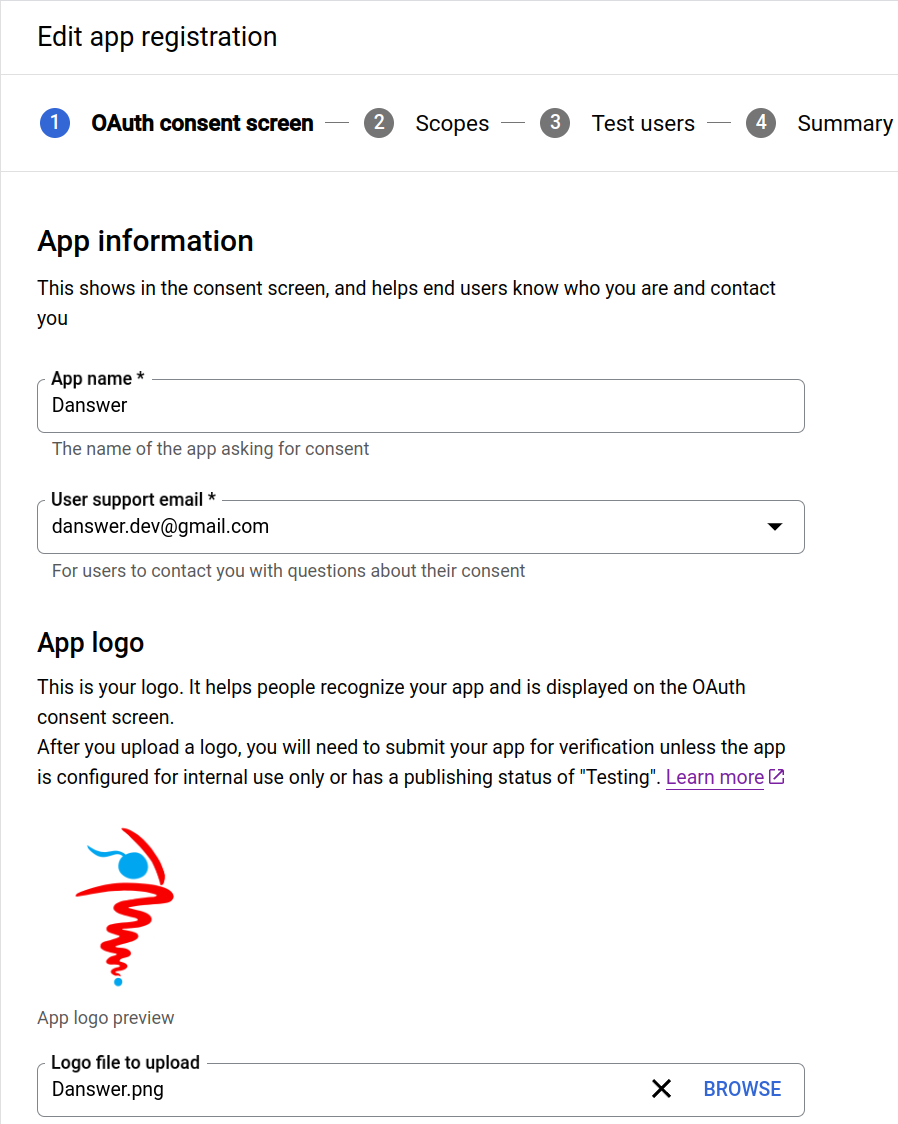 Leave the optional fields blank
Click SAVE AND CONTINUE
Leave the next two pages for Scopes and Test users blank.
Leave the optional fields blank
Click SAVE AND CONTINUE
Leave the next two pages for Scopes and Test users blank.
Setting up Credentials
Still under APIs & Services, go to Credentials on the left hand bar Click on +CREATE CREDENTIALS and chooseOAuth client ID
Select Web application then call it RECAP
Add a Authorized JavaScript origins as:
http://localhost:3000for local or replace withhttps://<WEB_DOMAIN>(e.g.https://www.RECAP.ai) if setting up for prod.
Authorized redirect URIs as:
http://localhost:3000/auth/oauth/callbackfor local setup orhttps://<WEB_DOMAIN>/auth/oauth/callbackif setting up for prod.
Turning on OAuth in RECAP
OAuth is controlled by 3 environment variables, regardless of deployment choice (non-containerized, docker compose, kubernetes). To turn the feature on set:AUTH_TYPE=google_oauthOAUTH_CLIENT_ID=<your client id from above>OAUTH_CLIENT_SECRET=<your client secret from above>- If setting up in production, then:
WEB_DOMAIN=<your domain including protocol e.g. https://www.RECAP.ai>
Non Containerized
Simply set the above environment variables when running the different RECAP processes.- The backend api server uses the 3 environment variables
- The frontend hits the api server to determine what user authentication setting is configured and serves the relevant pages.
Docker Compose
Simply set the 4 environment variables in a file called .env under RECAP/deployment/docker_compose.Kubernetes
Kubernetes deployment was designed for production use and assumes that user Auth is a required feature therefore it is on by default. To set up the required values, replace theREPLACE-THIS values in secrets.yaml with thebase64 encoded
client ID and client secret from above.